BCACTF
写在前面
国外的赛题还是挺有趣的,更偏脑洞一些。正值期末周,简单写两题当作娱乐放松了~。
MathJail - misc
描述
Just a fun python calculator! Good for math class.
解题
- 查看附件,如下。
1
2
3
4
5
6
7print("Welcome to your friendly python calculator!")
equation = input("Enter your equation below and I will give you the answer:\n")
while equation!="e":
answer = eval(equation, {"__builtins__":{}},{})
print(f"Here is your answer: {answer}")
equation = input("Enter your next equation below (type 'e' to exit):\n")
print("Goodbye!") - 考点为删除了
__builtins__的pyjail。参考 https://xz.aliyun.com/t/12647?time__1311=mqmhDvqIrrGNDQtiQGkI5YxWuFxjoOTD#toc-22 ,使用继承链条来绕过。
1 | |
magic - foren
描述
I found this piece of paper on the floor. I was going to throw it away, but it somehow screamed at me while I was holding it?!
hints: the pdf should be interactive; if not, try changing your pdf viewer
附件
https://arcs-s3-repo.nyc3.cdn.digitaloceanspaces.com/magic/magic.pdf
解题
- 打开
magic.pdf,发现可交互,推测内嵌了JavaScript脚本。 - 使用
Acrobat pdf reader打开,提取出一串混淆过的JavaScript代码。
1 | |
发现代码分为两部分,一部分为混淆加密字段的解密,另一部分
update()为flag验证函数。通过本地调试 + 调用解密函数可以大致还原
update()的面貌。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20function update() {
input = this.getField('A')['value'], ans = [];
for (var i = 0; i < input.length(); i++) {
ans['push'](input.charCodeAt(i) ^ parseInt(info['producer']) % (117 + i));
}
k = [
70, 45, 98, 17, 107, 76, 114, 95, 118, 56, 25, 40, 95, 49, 54, 99, 247, 177, 105, 42, 24, 94, 54, 1, 55, 58, 28, 5, 17, 86, 229, 123, 100, 44, 17, 20, 83, 90, 53, 23, 65, 98, 3
];
if (ans['length'] != k.length()) {
app.alert('Flag is incorrect!');
return;
}
for (var i = 0; i < k.length(); i++) {
if (ans[i] != k[i]) {
app.alert('Flag is incorrect!');
return;
}
}
app.alert('Flag is correct!');
}根据解密后的代码,已经知道了大概的逻辑,其中还有一个
parseInt(info['producer'])待解决。用010 hexEditor打开这个文件。搜索producer可以找到这样一串明文信息。1
2
3
4
5
6
7
8
942 0 obj
<<
/Author()/Title()/Subject()/Creator()/Producer(\376\377\0002\0008\0003\0005\0004\0008\0008\0009\0003\0002\0007\0004)/Keywords()
/CreationDate (D:20240528134825-04'00')
/ModDate (D:20240528134825-04'00')
/Trapped /False
/PTEX.Fullbanner (This is pdfTeX, Version 3.141592653-2.6-1.40.26 (TeX Live 2024/Arch Linux) kpathsea version 6.4.0)
>>
endobj询问gpt得知
Producer字段的内容是283548893274。故update()完整代码如下:
1 | |
- 使用
kmod283548893274 % (117 + i)得到原始flag1
2
3
4
5
6
7
8
9
10k = [
70, 45, 98, 17, 107, 76, 114, 95, 118, 56, 25, 40, 95, 49, 54, 99,
247, 177, 105, 42, 24, 94, 54, 1, 55, 58, 28, 5, 17, 86, 229, 123,
100, 44, 17, 20, 83, 90, 53, 23, 65, 98, 3
]
flag = ''
for i in range(len(k)):
char_code = k[i] ^ 283548893274 % (117 + i)
flag += str(chr(char_code))
print(flag)
Fogblaze
描述
Can you bypass this website’s new stateless CAPTCHA system?
Hints: The challengeId for “SCLN” would be 1e8298221a767bb37c01eb0cc61d1775
解题
进入网站后,发现需要验证码。
开启抓包,大写输入验证码后进入到一级目录。
抓包结果有两种类型的包。一种是初始化验证码。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16POST /captcha HTTP/1.1
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cache-Control: no-cache
Content-Length: 15
DNT: 1
Host: challs.bcactf.com:30311
Origin: http://challs.bcactf.com:30311
Pragma: no-cache
Proxy-Connection: keep-alive
Referer: http://challs.bcactf.com:30311/captcha?destination=/
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36 Edg/125.0.0.0
content-type: application/json
{"routeId":"/"}
返回的内容为captchaToken - 验证码token, image - 验证码图片base64, solved - 已解出题数, total - 总共题数, done - 是否通关
1 | |
另一种是解题数据包,请求头与上一种相同,但payload为
1 | |
需要captchaToken和word。
进入到一级目录后,尝试访问
The Flag,发现还是需要验证码,而且数量高达75个。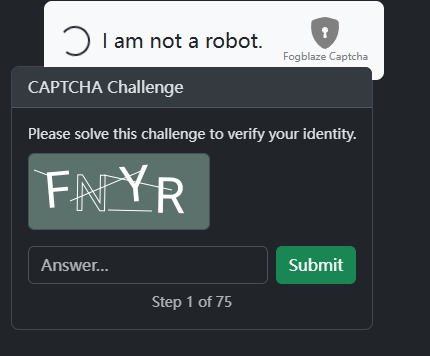
先试试人工打码,结果出现了时间限制。尝试使用ddddocr,但是识别率堪忧,而且只要中间出错,就要重新来。
这时候回头看了眼提示,发现1e8298221a767bb37c01eb0cc61d1775是SCLN的md5值,而且在token的第二部分,是题目相关信息的base64,其中就包含了challengeId。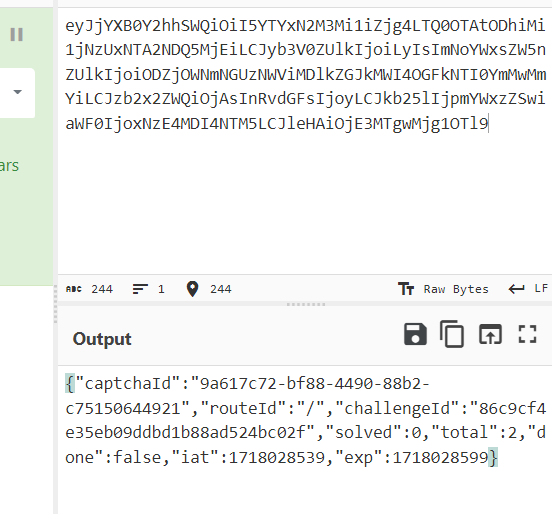
接下来生成爆破字典以及写写自动化脚本。
1
2
3
4
5
6
7
8
9import hashlib
with open("./hashes.txt", "w") as f:
for i in range(26):
for j in range(26):
for k in range(26):
for l in range(26):
s = chr(i + 65) + chr(j + 65) + chr(k + 65) + chr(l + 65)
f.write(s + " " + hashlib.md5(s.encode()).hexdigest() + "\n")
1 | |
- 访问链接
http://challs.bcactf.com:30311/flag?token={token}得到flag。
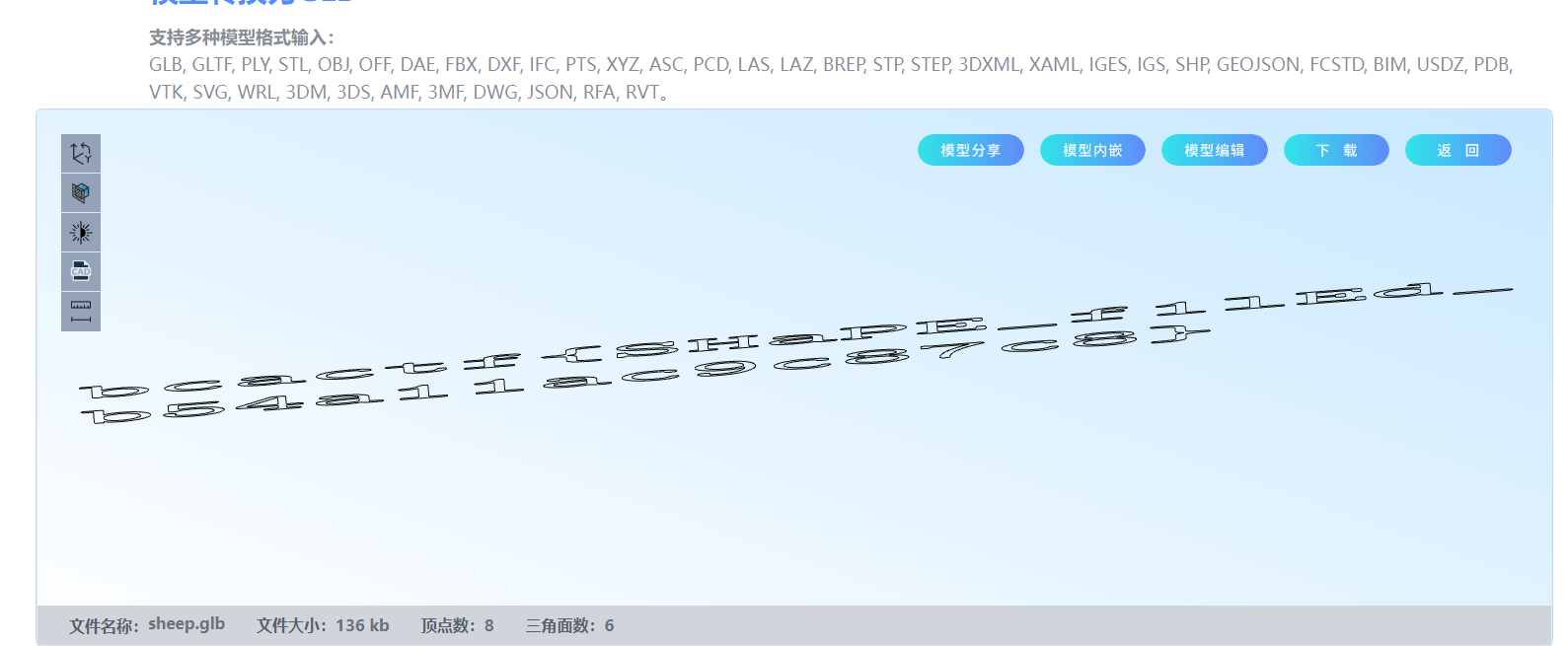
sheep
描述
baa
Hints: Figure out what type of file it is and see if there are tools you can use or modify.
附件
https://arcs-s3-repo.nyc3.cdn.digitaloceanspaces.com/sheep/sheep.shp
解题
参考 https://blog.csdn.net/wangming100110/article/details/133169695 ,.shp文件是一种矢量数据格式,用于存储GIS信息。
使用在线网站 https://3dconvert.nsdt.cloud/ 进行文件转换后预览,得到flag。